
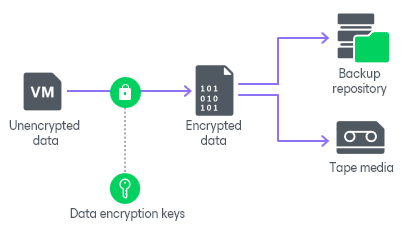
Architecture of Multimedia Encryption These encryption algorithms are... | Download Scientific Diagram
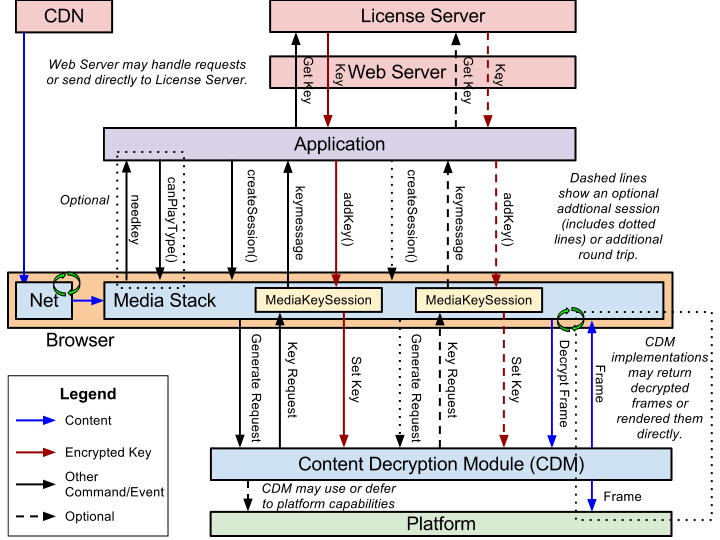
encrypted-media-encryption-scheme/explainer.md at main · WICG/encrypted- media-encryption-scheme · GitHub
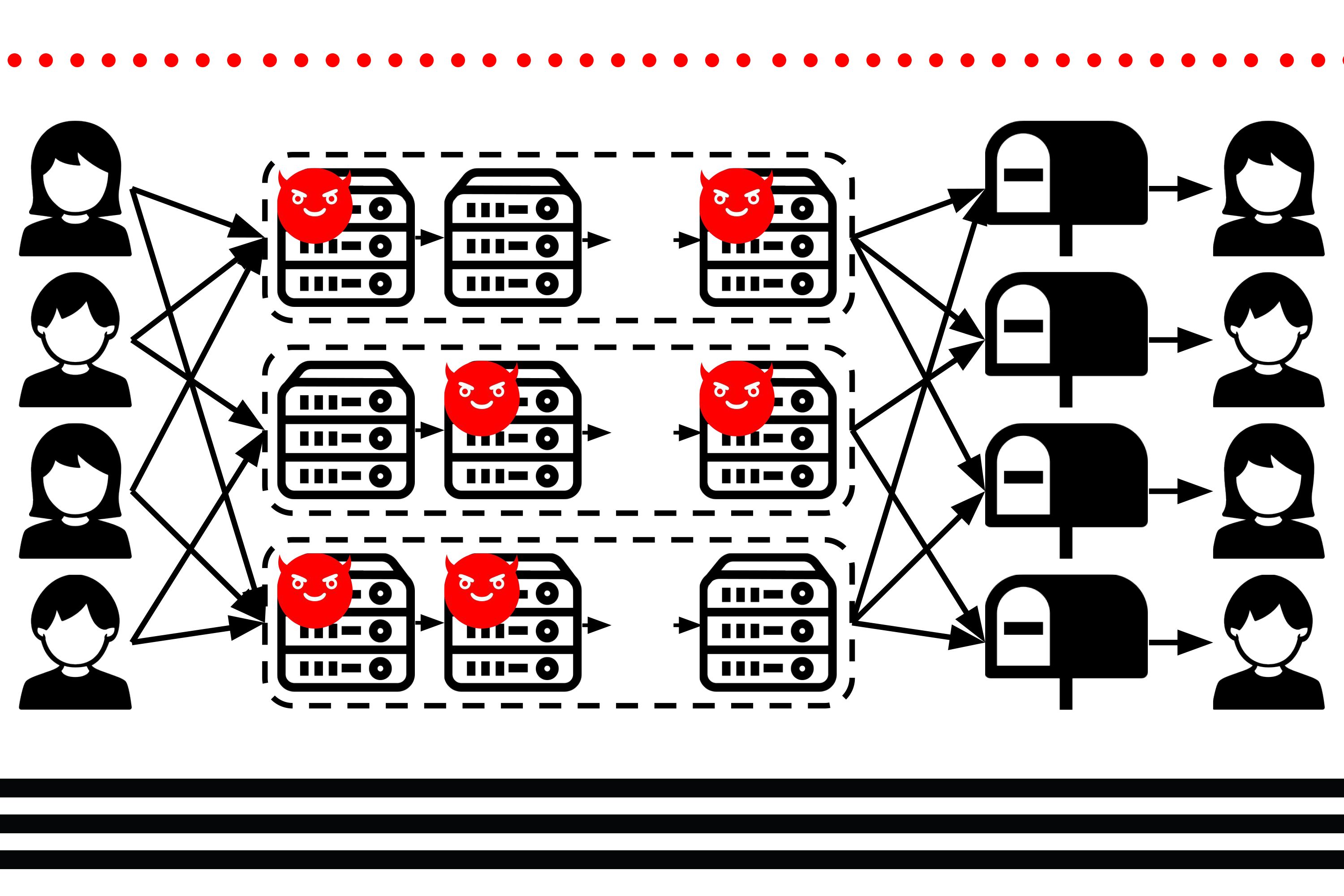
Protecting sensitive metadata so it can't be used for surveillance | MIT News | Massachusetts Institute of Technology








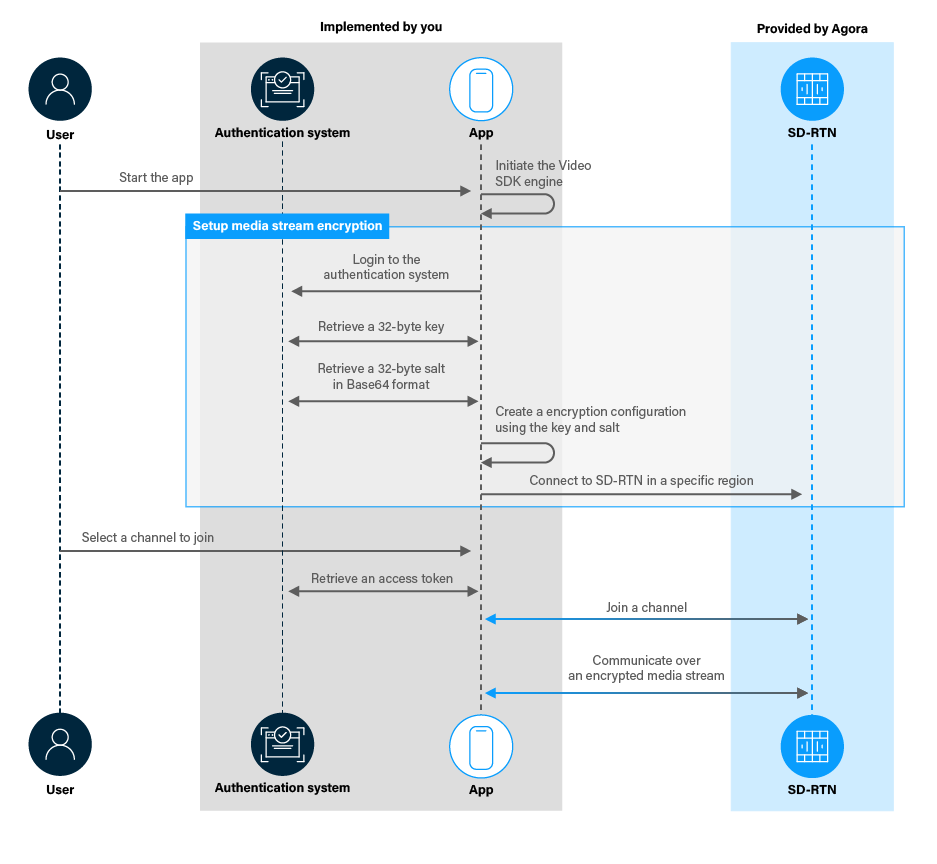

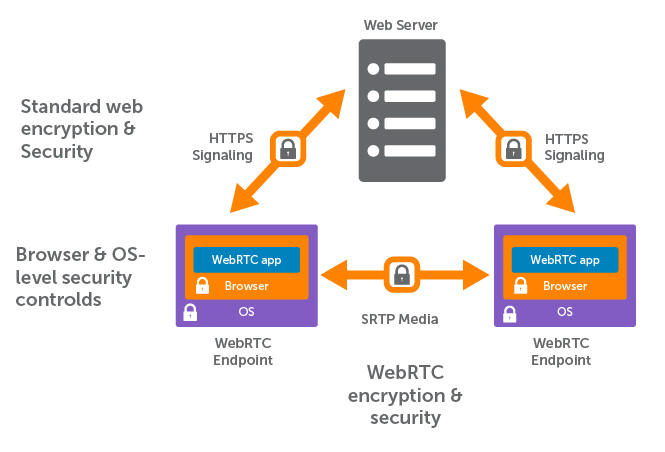

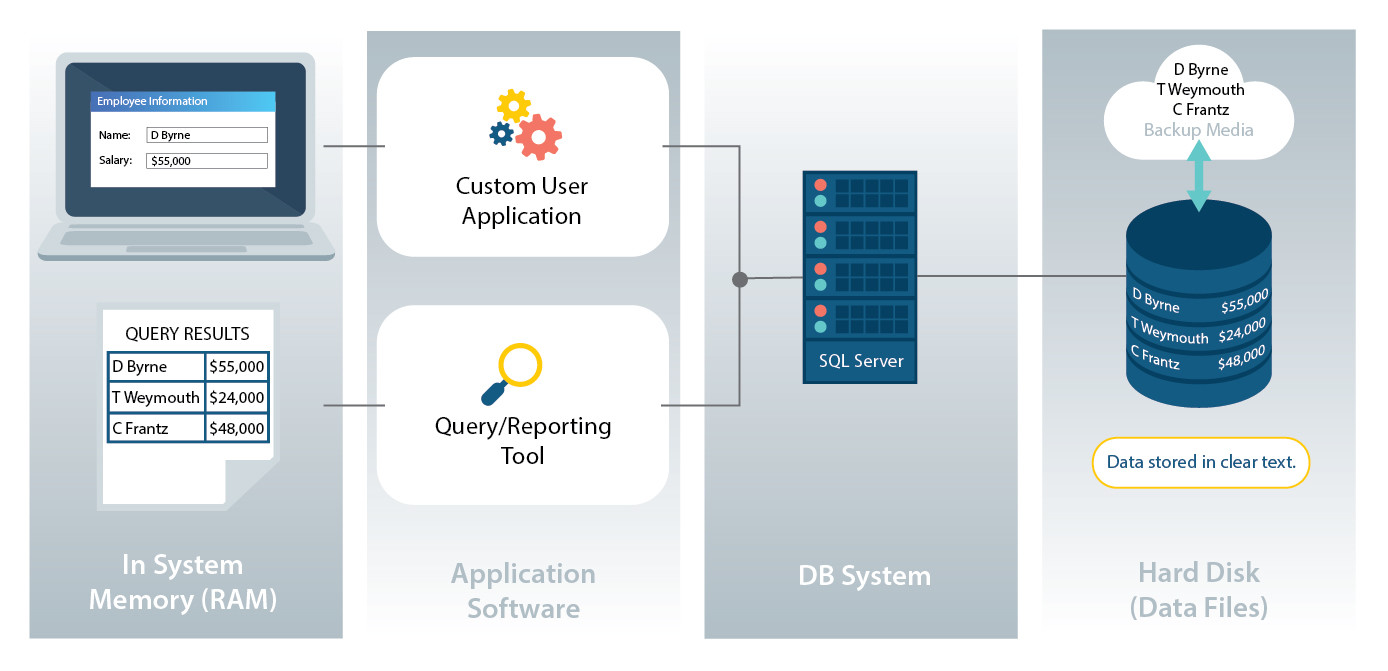

![KB7166] Decrypt a memory stick or external disk using ESET Endpoint Encryption KB7166] Decrypt a memory stick or external disk using ESET Endpoint Encryption](https://support.eset.com/storage/ESET/Platform/Publishing/images/Authoring/ImageFiles/ESET/KB_ENG/trash/deslock_KB7166_step2a.png)

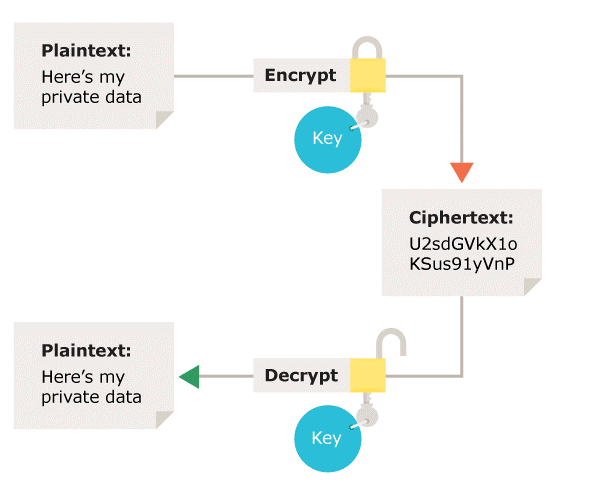

![KB7198] Encrypt a memory stick or external disk using ESET Endpoint Encryption KB7198] Encrypt a memory stick or external disk using ESET Endpoint Encryption](https://support.eset.com/storage/ESET/Platform/Publishing/images/Authoring/ImageFiles/ESET/KB_ENG/7198/KB7198Fig1-1a.png)